How To Summarize A Source
In computer programming, menstruation-based programming (FBP) is a programming paradigm that defines applications as networks of "black box" processes, which exchange data beyond predefined connections past message passing, where the connections are specified externally to the processes. These blackness box processes can exist reconnected endlessly to form different applications without having to be changed internally. FBP is thus naturally component-oriented.
FBP is a item form of dataflow programming based on bounded buffers, information packets with defined lifetimes, named ports, and separate definition of connections.
Introduction [edit]
Menses-based programming defines applications using the metaphor of a "data mill". Information technology views an awarding non as a single, sequential process, which starts at a point in time, and then does one thing at a time until information technology is finished, but as a network of asynchronous processes communicating past means of streams of structured data chunks, called "information packets" (IPs). In this view, the focus is on the awarding data and the transformations practical to it to produce the desired outputs. The network is defined externally to the processes, equally a list of connections which is interpreted by a piece of software, normally called the "scheduler".
The processes communicate by means of stock-still-capacity connections. A connectedness is attached to a process by means of a port, which has a name agreed upon between the process code and the network definition. More than one procedure can execute the aforementioned piece of lawmaking. At whatsoever point in time, a given IP can merely be "endemic" past a single procedure, or exist in transit between two processes. Ports may either be unproblematic, or array-type, as used e.g. for the input port of the Collate component described below. It is the combination of ports with asynchronous processes that allows many long-running primitive functions of data processing, such as Sort, Merge, Summarize, etc., to be supported in the course of software blackness boxes.
Because FBP processes can go along executing as long they have data to work on and somewhere to put their output, FBP applications generally run in less elapsed time than conventional programs, and brand optimal use of all the processors on a machine, with no special programming required to achieve this.[1]
The network definition is usually diagrammatic, and is converted into a connectedness listing in some lower-level linguistic communication or annotation. FBP is frequently a visual programming language at this level. More complex network definitions have a hierarchical construction, being built up from subnets with "glutinous" connections. Many other flow-based languages/runtimes are built around more traditional programming languages, the most notable[ citation needed ] example is RaftLib which uses C++ iostream-like operators to specify the menstruum graph.
FBP has much in common with the Linda[two] language in that it is, in Gelernter and Carriero's terminology, a "coordination language":[3] it is essentially language-contained. Indeed, given a scheduler written in a sufficiently low-level linguistic communication, components written in different languages tin can be linked together in a unmarried network. FBP thus lends itself to the concept of domain-specific languages or "mini-languages".
FBP exhibits "data coupling", described in the article on coupling as the loosest type of coupling betwixt components. The concept of loose coupling is in turn related to that of service-oriented architectures, and FBP fits a number of the criteria for such an architecture, albeit at a more than fine-grained level than near examples of this compages.
FBP promotes high-level, functional style of specifications that simplify reasoning nigh system behavior. An case of this is the distributed data flow model for constructively specifying and analyzing the semantics of distributed multi-party protocols.
History [edit]
Period-Based Programming was invented by J. Paul Morrison in the early 1970s, and initially implemented in software for a Canadian bank.[4] FBP at its inception was strongly influenced by some IBM simulation languages of the menses, in item GPSS, simply its roots go all the way dorsum to Conway's seminal newspaper on what he called coroutines.[v]
FBP has undergone a number of proper name changes over the years: the original implementation was called AMPS (Avant-garde Modular Processing Organization). 1 large application in Canada went alive in 1975, and, as of 2013, has been in continuous production apply, running daily, for almost 40 years. Because IBM considered the ideas behind FBP "too much like a constabulary of nature" to be patentable they instead put the bones concepts of FBP into the public domain, by means of a Technical Disclosure Bulletin, "Data Responsive Modular, Interleaved Task Programming System",[6] in 1971.[4] An article describing its concepts and feel using information technology was published in 1978 in the IBM Enquiry IBM Systems Periodical nether the name DSLM.[seven] A 2d implementation was washed as a articulation project of IBM Canada and IBM Nihon, nether the proper noun "Data Menses Development Director" (DFDM), and was briefly marketed in Nippon in the late '80s under the name "Data Flow Programming Manager".
Generally the concepts were referred to within IBM as "Data Flow", simply this term was felt to be too general, and eventually the name "Menstruation-Based Programming" was adopted.
From the early '80s to 1993 J. Paul Morrison and IBM builder Wayne Stevens refined and promoted the concepts behind FBP. Stevens wrote several manufactures describing and supporting the FBP concept, and included textile near it in several of his books.[8] [9] [ non-master source needed ] [10] [ not-main source needed ]. In 1994 Morrison published a volume describing FBP, and providing empirical evidence that FBP led to reduced evolution times.[11]
Concepts [edit]
The post-obit diagram shows the major entities of an FBP diagram (autonomously from the Information Packets). Such a diagram can exist converted straight into a list of connections, which can so be executed by an appropriate engine (software or hardware).
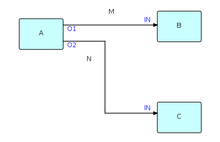
A, B and C are processes executing code components. O1, O2, and the two INs are ports connecting the connections Thousand and N to their corresponding processes. It is permitted for processes B and C to be executing the same code, so each procedure must have its own set of working storage, control blocks, etc. Whether or not they practise share code, B and C are free to utilize the same port names, every bit port names but have pregnant within the components referencing them (and at the network level, of grade).
M and N are what are often referred to as "bounded buffers", and have a fixed capacity in terms of the number of IPs that they tin concord at whatsoever signal in fourth dimension.
The concept of ports is what allows the aforementioned component to exist used at more than one identify in the network. In combination with a parametrization ability, called Initial Information Packets (IIPs), ports provide FBP with a component reuse ability, making FBP a component-based architecture. FBP thus exhibits what Raoul de Campo and Nate Edwards of IBM Research take termed configurable modularity.
Information Packets or IPs are allocated in what might be chosen "IP space" (just as Linda'south tuples are allocated in "tuple space"), and have a well-divers lifetime until they are disposed of and their space is reclaimed - in FBP this must be an explicit activity on the part of an owning process. IPs traveling across a given connection (actually it is their "handles" that travel) plant a "stream", which is generated and consumed asynchronously - this concept thus has similarities to the lazy cons concept described in the 1976 commodity by Friedman and Wise.[12]
IPs are unremarkably structured chunks of data - some IPs, however, may non contain any real data, merely are used simply every bit signals. An example of this is "bracket IPs", which can be used to group data IPs into sequential patterns within a stream, called "substreams". Substreams may in turn be nested. IPs may besides be chained together to form "IP copse", which travel through the network as unmarried objects.
The system of connections and processes described above can exist "ramified" to any size. During the development of an awarding, monitoring processes may be added between pairs of processes, processes may be "exploded" to subnets, or simulations of processes may exist replaced by the existent process logic. FBP therefore lends itself to rapid prototyping.
This is really an assembly line image of data processing: the IPs travelling through a network of processes may exist thought of as widgets travelling from station to station in an assembly line. "Machines" may easily be reconnected, taken off line for repair, replaced, and and so on. Oddly enough, this image is very like to that of unit record equipment that was used to process data before the days of computers, except that decks of cards had to be hand-carried from ane machine to some other.
Implementations of FBP may be non-preemptive or preemptive - the earlier implementations tended to exist non-preemptive (mainframe and C language), whereas the latest Java implementation (meet below) uses Java Thread class and is preemptive.
Examples [edit]
"Telegram Problem" [edit]
FBP components often form complementary pairs. This instance uses 2 such pairs. The problem described seems very simple as described in words, merely in fact is surprisingly difficult to accomplish using conventional procedural logic. The task, chosen the "Telegram Problem", originally described by Peter Naur, is to write a program which accepts lines of text and generates output lines containing every bit many words as possible, where the number of characters in each line does not exceed a sure length. The words may not be split and we assume no word is longer than the size of the output lines. This is coordinating to the give-and-take-wrapping problem in text editors.[thirteen]
In conventional logic, the developer speedily discovers that neither the input nor the output structures tin be used to drive the phone call bureaucracy of control flow. In FBP, on the other paw, the problem description itself suggests a solution:
- "words" are mentioned explicitly in the description of the problem, so it is reasonable for the designer to treat words equally information packets (IPs)
- in FBP there is no single phone call hierarchy, so the programmer is not tempted to forcefulness a sub-pattern of the solution to be the superlative level.
Here is the almost natural solution in FBP (at that place is no single "correct" solution in FBP, but this seems like a natural fit):

Peter Naur's "Telegram problem"
where DC and RC stand for "DeCompose" and "ReCompose", respectively.
Every bit mentioned in a higher place, Initial Information Packets (IIPs) can be used to specify parametric information such as the desired output record length (required by the rightmost two components), or file names. IIPs are data chunks associated with a port in the network definition which become "normal" IPs when a "receive" is issued for the relevant port.
Batch update [edit]
This type of program involves passing a file of "details" (changes, adds and deletes) confronting a "main file", and producing (at to the lowest degree) an updated primary file, and i or more reports. Update programs are more often than not quite hard to code using synchronous, procedural code, as two (sometimes more than) input streams have to be kept synchronized, fifty-fifty though there may exist masters without corresponding details, or vice versa.

Canonical "batch update" structure
In FBP, a reusable component (Collate), based on the unit record thought of a Collator, makes writing this type of awarding much easier equally Collate merges the two streams and inserts bracket IPs to signal grouping levels, significantly simplifying the downstream logic. Suppose that ane stream ("masters" in this example) consists of IPs with key values of 1, 2 and 3, and the 2nd stream IPs ("details") have fundamental values of eleven, 12, 21, 31, 32, 33 and 41, where the outset digit corresponds to the master fundamental values. Using bracket characters to correspond "bracket" IPs, the collated output stream will be as follows:
( m1 d11 d12 ) ( m2 d21 ) ( m3 d31 d32 d33 ) (d41)
As there was no master with a value of 4, the last group consists of a single detail (plus brackets).
The structure of the above stream can be described succinctly using a BNF-like notation such equally
{ ( [m] d* ) }* Collate is a reusable black box which only needs to know where the command fields are in its incoming IPs (even this is not strictly necessary equally transformer processes can be inserted upstream to place the control fields in standard locations), and can in fact be generalized to whatsoever number of input streams, and any depth of subclass nesting. Collate uses an array-type port for input, allowing a variable number of input streams.
Multiplexing processes [edit]
Period-based programming supports process multiplexing in a very natural way. Since components are read-only, any number of instances of a given component ("processes") tin run asynchronously with each other.

When computers usually had a single processor, this was useful when a lot of I/O was going on; at present that machines normally accept multiple processors, this is starting to become useful when processes are CPU-intensive besides. The diagram in this department shows a single "Load Balancer" process distributing data between 3 processes, labeled S1, S2 and S3, respectively, which are instances of a unmarried component, which in turn feed into a single process on a "get-go-come, first served" basis.
Simple interactive network [edit]

Schematic of general interactive application
In this full general schematic, requests (transactions) coming from users enter the diagram at the upper left, and responses are returned at the lower left. The "back ends" (on the correct side) communicate with systems at other sites, e.one thousand. using CORBA, MQSeries, etc. The cross-connections represent requests that practise not need to get to the back ends, or requests that have to cycle through the network more than once before being returned to the user.
As different requests may employ different dorsum-ends, and may require differing amounts of fourth dimension for the back-ends (if used) to process them, provision must be made to chronicle returned data to the appropriate requesting transactions, e.g. hash tables or caches.
The to a higher place diagram is schematic in the sense that the final application may incorporate many more than processes: processes may be inserted between other processes to manage caches, display connection traffic, monitor throughput, etc. Too the blocks in the diagram may represent "subnets" - modest networks with 1 or more open connections.
Comparing with other paradigms and methodologies [edit]
Jackson Structured Programming (JSP) and Jackson System Development (JSD) [edit]
This methodology assumes that a program must be structured as a single procedural hierarchy of subroutines. Its starting bespeak is to describe the application as a set of "main lines", based on the input and output data structures. One of these "main lines" is and then called to drive the whole program, and the others are required to be "inverted" to turn them into subroutines (hence the name "Jackson inversion"). This sometimes results in what is called a "disharmonism", requiring the program to be split into multiple programs or coroutines. When using FBP, this inversion process is not required, equally every FBP component tin be considered a split "primary line".
FBP and JSP share the concept of treating a program (or some components) as a parser of an input stream.
In Jackson'due south later on piece of work, Jackson Arrangement Development (JSD), the ideas were developed further.[14] [fifteen]
In JSD the design is maintained equally a network blueprint until the final implementation stage. The model is and so transformed into a set of sequential processes to the number of available processors. Jackson discusses the possibility of directly executing the network model that exists prior to this step, in section 1.three of his book (italics added):
- The specification produced at the end of the System Timing step is, in principle, capable of direct execution. The necessary environment would contain a processor for each process, a device equivalent to an unbounded buffer for each information stream, and some input and output devices where the arrangement is connected to the real world. Such an environment could, of class, be provided by suitable software running on a sufficiently powerful automobile. Sometimes, such directly execution of the specification will be possible, and may fifty-fifty be a reasonable choice. [xv]
FBP was recognized past M A Jackson as an arroyo that follows his method of "Program decomposition into sequential processes communicating past a coroutine-like mechanism"[16]
Applicable programming [edit]
W.B. Ackerman defines an applicable linguistic communication as one which does all of its processing past means of operators applied to values.[17] The earliest known applicable linguistic communication was LISP.
An FBP component tin be regarded equally a part transforming its input stream(southward) into its output stream(southward). These functions are then combined to brand more than complex transformations, as shown here:

2 functions feeding i
If nosotros label streams, as shown, with lower instance letters, then the to a higher place diagram can be represented succinctly as follows:
c = G(F(a),F(b));
Just as in functional notation F can be used twice considering it but works with values, and therefore has no side effects, in FBP two instances of a given component may be running meantime with each other, and therefore FBP components must not have side-effects either. Functional notation could clearly exist used to represent at least a part of an FBP network.
The question so arises whether FBP components can themselves be expressed using functional notation. Due west.H. Burge showed how stream expressions can be developed using a recursive, applicable style of programming, but this work was in terms of (streams of) atomic values.[eighteen] In FBP, it is necessary to be able to describe and process structured data chunks (FBP IPs).
Furthermore, most applicable systems assume that all the information is available in memory at the same time, whereas FBP applications need to be able to process long-running streams of data while still using finite resources. Friedman and Wise suggested a manner to do this by adding the concept of "lazy cons" to Burge's work. This removed the requirement that both of the arguments of "cons" be bachelor at the same instant of time. "Lazy cons" does non really build a stream until both of its arguments are realized - before that it merely records a "promise" to do this. This allows a stream to be dynamically realized from the forepart, only with an unrealized dorsum stop. The end of the stream stays unrealized until the very end of the process, while the kickoff is an ever-lengthening sequence of items.
Linda [edit]
Many of the concepts in FBP seem to accept been discovered independently in dissimilar systems over the years. Linda, mentioned above, is ane such. The difference between the ii techniques is illustrated by the Linda "school of piranhas" load balancing technique - in FBP, this requires an extra "load balancer" component which routes requests to the component in a list which has the smallest number of IPs waiting to be processed. Clearly FBP and Linda are closely related, and one could easily exist used to simulate the other.
Object-oriented programming [edit]
An object in OOP tin exist described every bit a semi-autonomous unit comprising both information and behaviour. Objects communicate by ways of "method calls", which are essentially subroutine calls, done indirectly via the form to which the receiving object belongs. The object'southward internal data can only be accessed past means of method calls, so this is a class of information hiding or "encapsulation". Encapsulation, notwithstanding, predates OOP - David Parnas wrote one of the seminal articles on it in the early 70s[nineteen] - and is a basic concept in computing. Encapsulation is the very essence of an FBP component, which may exist thought of as a black box, performing some conversion of its input information into its output data. In FBP, part of the specification of a component is the information formats and stream structures that it can accept, and those it will generate. This constitutes a grade of design by contract. In improver, the data in an IP tin can simply exist accessed direct past the currently owning process. Encapsulation can also be implemented at the network level, by having outer processes protect inner ones.
A paper by C. Ellis and S. Gibbs distinguishes between active objects and passive objects.[20] Passive objects contain information and behaviour, as stated in a higher place, but they cannot determine the timing of this behaviour. Agile objects on the other hand can do this. In their commodity Ellis and Gibbs land that agile objects take much more potential for the development of maintainable systems than do passive objects. An FBP awarding tin can be viewed as a combination of these two types of object, where FBP processes would stand for to active objects, while IPs would correspond to passive objects.
Role player model [edit]
FBP considers Carl Hewitt's Actor as an asynchronous processes with ii ports: ane for input messages and one for control signals. A command betoken is emitted past the role player itself after each round of execution. The purpose of this signal is to avoid parallel execution of the role player'due south trunk and so to allow to access the fields of the actor object without synchronization.
Encounter also [edit]
- Active objects
- Actor model
- Apache NiFi
- BMDFM
- Communicating Sequential Processes (CSP)
- Concurrent computing
- Dataflow
- Data catamenia diagram
- Dataflow programming
- FBD - Function Block Diagrams (a programming linguistic communication in the IEC 61131 standard)
- Functional reactive programming
- Linda (coordination language)
- Low-lawmaking development platforms
- MapReduce
- Node-RED
- Pipeline programming
- Wayne Stevens
- XProc
- Yahoo Pipes
References [edit]
- ^ "Flow-based Programming".
- ^ Carriero, Nicholas; Gelernter, David (1989). "Linda in context". Communications of the ACM. 32 (4): 444–458. doi:10.1145/63334.63337. S2CID 5900105.
- ^ Gelernter, David; Carriero, Nicholas (1992). "Coordination languages and their significance". Communications of the ACM. 35 (2): 97–107. doi:10.1145/129630.129635. S2CID 7748555.
- ^ a b Gabe Stein (August 2013). "How an Arcane Coding Method From 1970s Banking Software Could Save the Sanity of Web Developers Everywhere". Retrieved 24 Jan 2016.
- ^ Conway, Melvin E. (1963). "Pattern of a separable transition-diagram compiler". Communications of the ACM. 6 (7): 396–408. doi:ten.1145/366663.366704. S2CID 10559786.
- ^ J. Paul Morrison, Data Responsive Modular, Interleaved Task Programming Arrangement, IBM Technical Disclosure Message, Vol. 13, No. 8, 2425-2426, Jan 1971
- ^ Morrison, J. P. (1978). "Data Stream Linkage Mechanism". IBM Systems Periodical. 17 (4): 383–408. doi:10.1147/sj.174.0383.
- ^ Stevens, Due west. P. (1982). "How data flow tin can improve application development productivity". IBM Systems Journal. 21 (2): 162–178. doi:10.1147/sj.212.0162.
- ^ West.P. Stevens, Using Data Flow for Awarding Evolution, Byte, June 1985
- ^ W.P. Stevens, Software Pattern - Concepts and Methods, Practical Software Applied science Series, Ed. Allen Macro, Prentice Hall, 1990, ISBN 0-13-820242-seven
- ^ Johnston, Wesley M.; Hanna, J. R. Paul; Millar, Richard J. (2004). "Advances in dataflow programming languages". ACM Computing Surveys. 36 (ane): 1–34. CiteSeerX10.1.1.99.7265. doi:ten.1145/1013208.1013209. S2CID 5257722.
- ^ D.P. Friedman and D.S. Wise, CONS should non evaluate its arguments, Automata, Languages and Programming, Edinburgh Academy Press, Edinburgh, 1976
- ^ "Peter Naur's "Telegram Problem"". Archived from the original on 2014-09-06. Retrieved 2014-09-06 .
- ^ "Programming" by M. A. Jackson, published in Proceedings of Workshop on Software in Loftier-Energy Physics, pages ane-12, CERN, Geneva, four–6 October 1982
- ^ a b "A Organisation development method Archived 2012-02-06 at the Wayback Auto" past M. A. Jackson, published in Tools and notions for program construction: An advanced course, Cambridge University Printing, 1982
- ^ "JSP In Perspective" Michael Jackson; JSP in Perspective; in Software Pioneers: Contributions to Software Engineering; Manfred Broy, Ernst Denert eds; Springer, 2002
- ^ Westward.B. Ackerman, Data Period Languages, Proceedings National Computer Conference, pp. 1087-1095, 1979
- ^ W.H. Burge, Recursive Programming Techniques, Addison-Wesley, Reading, MA, 1975
- ^ Parnas, D. L. (1972). "On the criteria to exist used in decomposing systems into modules". Communications of the ACM. 15 (12): 1053–1058. doi:ten.1145/361598.361623. S2CID 53856438.
- ^ C. Ellis and South. Gibbs, Agile Objects: Realities and Possibilities, in Object-Oriented Concepts, Databases, and Applications, eds. W. Kim and F.H. Lochovsky, ACM Press, Addison-Wesley, 1989
External links [edit]
- Razdow, Allen (Dec 1997). "Building Enterprise Data Refineries". DMReview . Retrieved 2006-07-15 .
- Mayer, Anthony; McGough, Stephen; Gulamali, Murtaza; Young, Laurie; Stanton, Jim; Newhouse, Steven; Darlington, John (2002). "Meaning and Behaviour in Grid Oriented Components" (PDF). London e-Scientific discipline Heart, Purple College of Science, Technology and Medicine. Archived from the original (PDF) on 2012-02-04.
- Black, Andrew P.; Huang, Jie; Koster, Rainer; Walpole, Jonathan; Pu, Calton (2002). "Infopipes: An abstraction for multimedia streaming" (PDF). Multimedia Systems. Springer-Verlag. 8 (5): 406–419. doi:10.1007/s005300200062. S2CID 5700383. Retrieved 2006-08-10 .
- Kra, David (October 2004). "zSeries and iSeries servers in the grid domain". IBM DeveloperWorks . Retrieved 2006-07-thirteen .
- Ludäscher, Bertram; Altintas, Ilkay; Berkley, Republic of chad; et al. (September 2004). "Scientific Workflow Direction and the Kepler System" (PDF). San Diego Supercomputer Center. Retrieved 2006-07-xiv .
- Bickle, Jerry; Richardson, Kevin; Smith, Jeff (2005). "OMG Software Radio Specification Overview for Robotics" (PDF). Object Management Grouping - Software-Based Communications. Archived from the original (PDF) on 2006-07-14. Retrieved 2006-07-15 .
- Blažević, Mario (2006). "Streaming Component Combinators". Proceedings of Extreme Markup Languages. Archived from the original on 2007-09-xviii. Retrieved 2006-eleven-09 .
- Kauler, Barry (1999). Flow Design for Embedded Systems, 2nd Edition. R&D Books/Miller Freeman. ISBN978-0-87930-555-0.
- Us patent 5204965, Guthery, Scott B.; Barth, Paul Southward. & Barstow, David R., "Data processing system using stream stores", issued 1993-04-twenty, assigned to Schlumberger Engineering science Corporation
- Morrison, J. Paul (March 2013). "Menstruum-Based Programming". Application Developers' News (1). Retrieved 2014-05-25 .
- Staplin, George Peter (2006). "Tcl Catamenia-Based Programming - TFP". Retrieved 2010-10-07 .
- Johnston, Wesley M.; Hanna, J. R. Paul; Millar, Richard J. (March 2004). "Advances in dataflow programming languages". ACM Calculating Surveys. 36 (i): ane–34. doi:10.1145/1013208.1013209. S2CID 5257722.
- Koster, Rainer; Black, Andrew P.; Huang, Jie; Walpole, Jonathan; Pu, Calton (April 2003). "Thread transparency in information menses middleware". Software: Practice and Feel. 33 (4): 321–349. CiteSeerXx.1.1.15.3933. doi:10.1002/spe.510. S2CID 37356020. Retrieved 2006-12-05 .
- Stevenson, Tony (February 1995). "Review of "Flow-Based Programming"". PC Update, the magazine of Melbourne PC User Group, Australia. Archived from the original on 2006-09-25. Retrieved 2006-12-06 .
- Lea, Doug (May 2001). "Composing Oneway Messages". Retrieved 2006-12-06 .
- Bowers, Shawn; Ludäscher, B.; Ngu, A.H.H.; Critchlow, T. "Enabling Scientific Workflow Reuse through Structured Limerick of Dataflow and Control-Catamenia" (PDF). SciFlow '06. Archived from the original (PDF) on 2007-02-05. Retrieved 2006-12-06 .
- Sorber, Jacob; Kostadinov, Alexander; Garber, Matthew; Brennan, Matthew; Corner, Marking D.; Berger, Emery D. (2007). "Eon". Eon: a language and runtime system for perpetual systems. Proceedings of the 5th international conference on Embedded networked sensor systems - Session: Ability direction. p. 161. doi:10.1145/1322263.1322279. ISBN9781595937636. S2CID 12851752.
- Fiedler, Lars; Dasey, Timothy (2014). "Systems and Methods for Composable Analytics". National Technical Information Service. Retrieved 2014-04-01 .
- Matt, Carkci (2014). Dataflow and Reactive Programming Systems: A Practical Guide. CreateSpace Contained Publishing Platform. ISBN978-1497422445.
How To Summarize A Source,
Source: https://en.wikipedia.org/wiki/Flow-based_programming
Posted by: rossarishe.blogspot.com


0 Response to "How To Summarize A Source"
Post a Comment